How to successfully manage your mobile Cyber Risks
We live in a digital world
Our smartphone: the modern Swiss army knife
We live in a digital world – more than ever. This is best demonstrated by a piece of hardware that is now used by over 96% of the working population: The smartphone. In our private lives as well as in business, it is our daily companion: It navigates us to our destination, reminds us of our appointments and whether we need an umbrella on the road. Access to emails and documents are a matter of course anyway, and the number of available useful (and less useful) apps grows daily. Hardly any other device combines so many functions, from a digital wallet to a camera, and no other device is used so frequently (3.7 hours a day on average). In this respect, it is only logical that companies are also increasingly recognizing the opportunities offered by the use of mobile devices:
- Better accessibility, improved collaboration between teams
- Increased efficiency, greater flexibility
- Potential for cost savings
- Basis for multi-factor authentication (MFA)
- Basis for use of enterprise apps
Hidden risks in mobile use
Often disregarded in cyber risk management are the risks that arise in particular from the use of mobile devices. This is despite the fact that 45% of companies experienced a cyber incident involving a mobile device last year (according to the Verizon Mobile Security Index Report 2022).
In contrast to a classic office workplace, a mobile device is much more exposed to cyber threats (Remote working, e.g., via insecure WLAN connections in public, no shutdown after office hours, merging of private and business use).
It is much easier for us to fall into the trap of phishing attempts on our smartphones, partly for technical reasons (e.g., no mouse-over where we can see the link URL), but also because we are less attentive when we are on the move. In addition, there are malicious apps (e.g., Hiddad, AlienBot), spyware, or vulnerability exploits that can pose a threat to us.
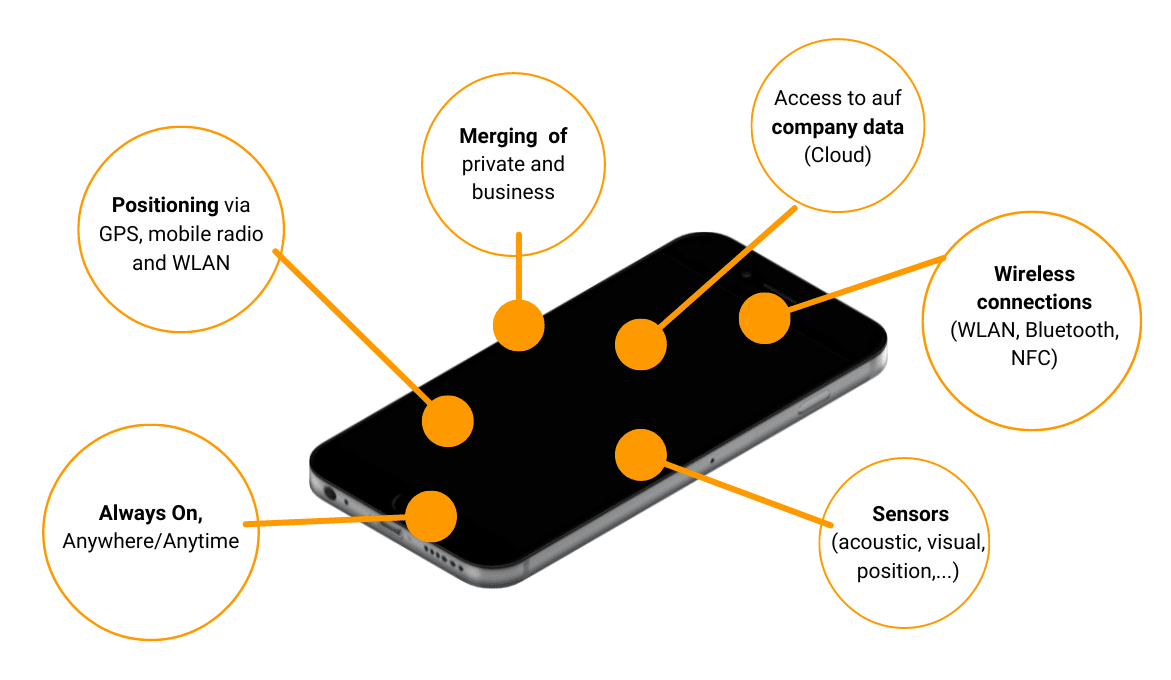
Risks associated with smartphone use
Mobile Cyber Risk Management:
How can companies successfully counter the risk posed by mobile devices at management level? We often see that selective measures are taken (e.g., with the help of security software or policies assigned in MDM). However, this does not provide a holistic view of the risks for the company. If the wrong measures are taken or if they are not targeted, costs are rising up without added value. On the other hand, essential risks can remain undetected and therefore cause significantly greater damage.
Cyber risk management shows and evaluates the risks and makes it possible to move the topic from a purely operational task to management. The risks become visible and assessable and the management can decide on suitable strategies and measures.
Successful cyber risk management includes the following five steps:
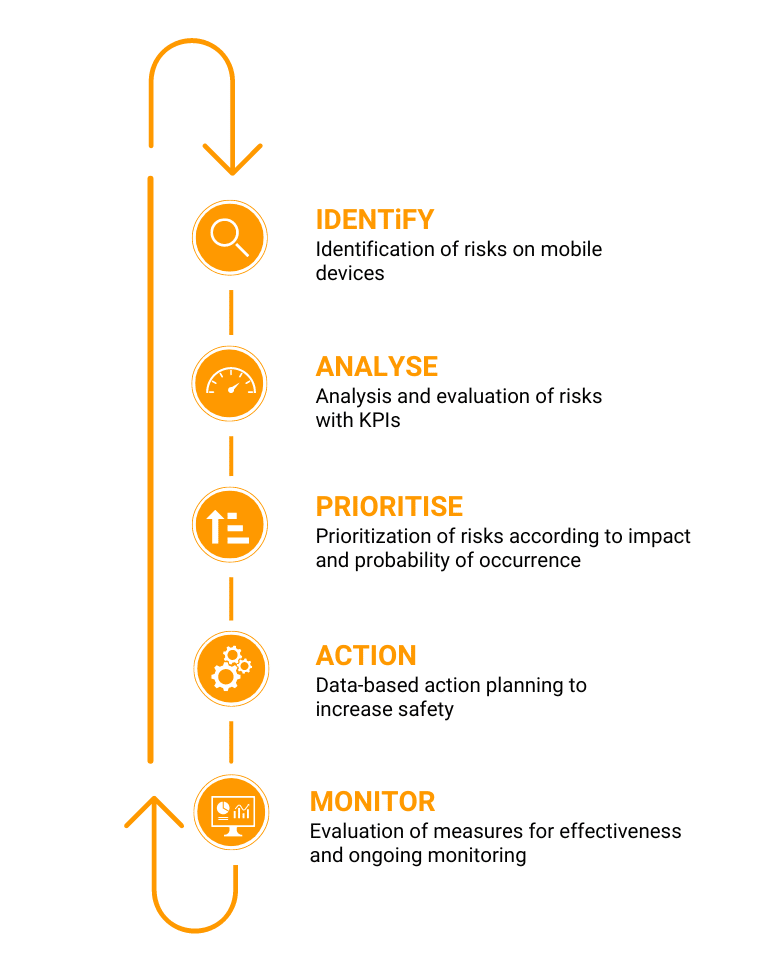
Risk Management Framework (based on NIST RMF)
What does cyber risk management require?
1. Cyber Risk Communication
Cyber risk success is the result of good collaboration at various levels of the company: from management to budget and security officers and digitization experts to the IT team, everyone has a part to play. The prerequisite for constructive collaboration lies in transparent and comprehensible communication across all functional levels.
How can better communication be achieved?
Clear and uniform key risk indicators (KRIs) and reports that reduce complexity help management and IT to jointly understand where action is needed and financial investments are required.
2. Cyber Risk Visualization
A picture says more than 1000 words? This is not new – and yet we often have to slog through long columns of letters, and are often no smarter afterwards than before. A good visualization (e.g. in a dashboard) provides an overview of the risks in the company that can be quickly understood by all levels. Appropriate representations (e.g. trend curves, frequency and distribution of risks, criticality,…) provide a meaningful picture of the situation. Cyber risk management can thus assume much stronger control and advisory functions.
3. Cyber Risk Insights
Data, data, data: At no time has more data been produced than now, and the trend is rising. Making proper use of this multitude of data is the great challenge of our time.
The multitude of information on the risk of mobile devices, on cyber threats, on vulnerabilities that have occurred must be compiled and used to identify, evaluate and classify risks.
The key is to automate these steps and deploy experts where they can bring their human strengths to bear: In the context of the identified risks to the company and in the control of security measures: Organizational, technical and strategic.
4. Cyber Risk Result
In the end, it is the result and the proof of success that counts – this is especially true for management tasks. Determining the effectiveness of measures taken is essential for cyber risk management: Only those who can see whether and how well measures are working and actually contributing to a reduction in risk can meaningfully evaluate and, if necessary, optimize them.
A look into the future
A change in security strategy will be necessary for companies to keep pace with real-world developments. Although the budget for security as a whole is being expanded at companies, a large part of the attention still lies with the (often static) security measures that affect PCs and servers. The reality is that the trend is clearly towards mobile solutions – from PCs to mobile devices, from on-premise solutions to the cloud. Those who do not include the risks of mobile devices in their command center on cyber risks are leaving out an ever-growing part of the possible attack vectors and risk factors – the higher the probability of a cyber incident increases in return.
Modern digital management dashboards provide the technical foundation for successful cyber risk management. Rethinking risk strategy offers companies the opportunity to chart a successful path for the future.